Penetration testing target: pentest.id
The basic penetration testing process was used for this project. There were 4 processes: Discovery/Reconnaissance, Scanning, Exploitation, and Post-Exploitation. (5 Important Questions to Ask Your Next Penetration Tester, 2015).
The main purpose of this testing:
- Discover the vulnerabilities based on the findings using certain tools that provide us with certain information that is visible only by enumerating the website with blackbox approach.
- Attempt to break into the website using the vulnerabilities discovered.
The tools used for this testing:
Online platforms:
- Pentest-Tools.com
- Sucuri
- UpGuard
- Observatory
- Censys
Kali Linux tools:
- Nikto
- Whatweb
- Nmap
- Owasp Zap
- Skipfish
- Wpscan
- Cupp
- Metasploit
I found quite a lot of findings but I could not explain it all in this blog. So, I only showed some of the findings below using some tools mention above.
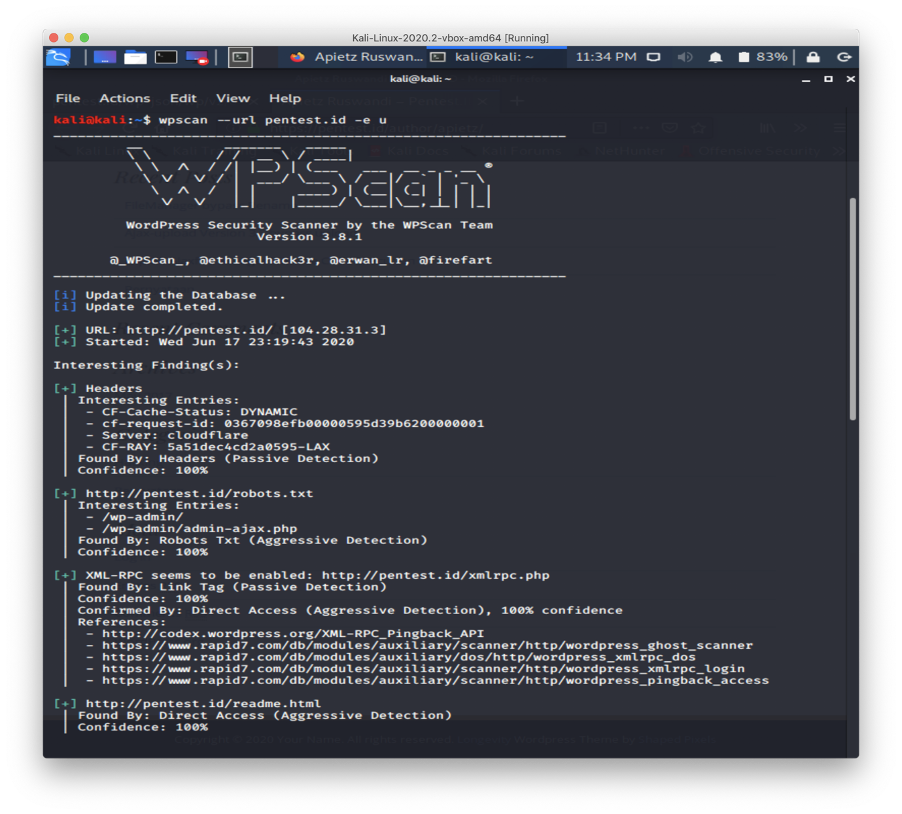
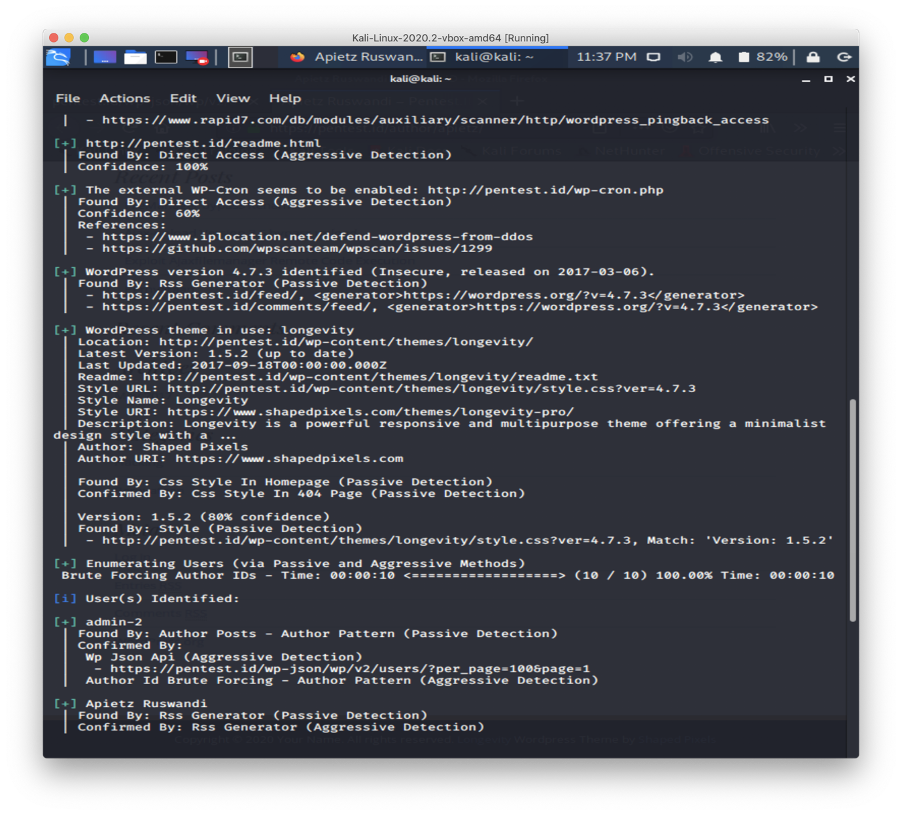
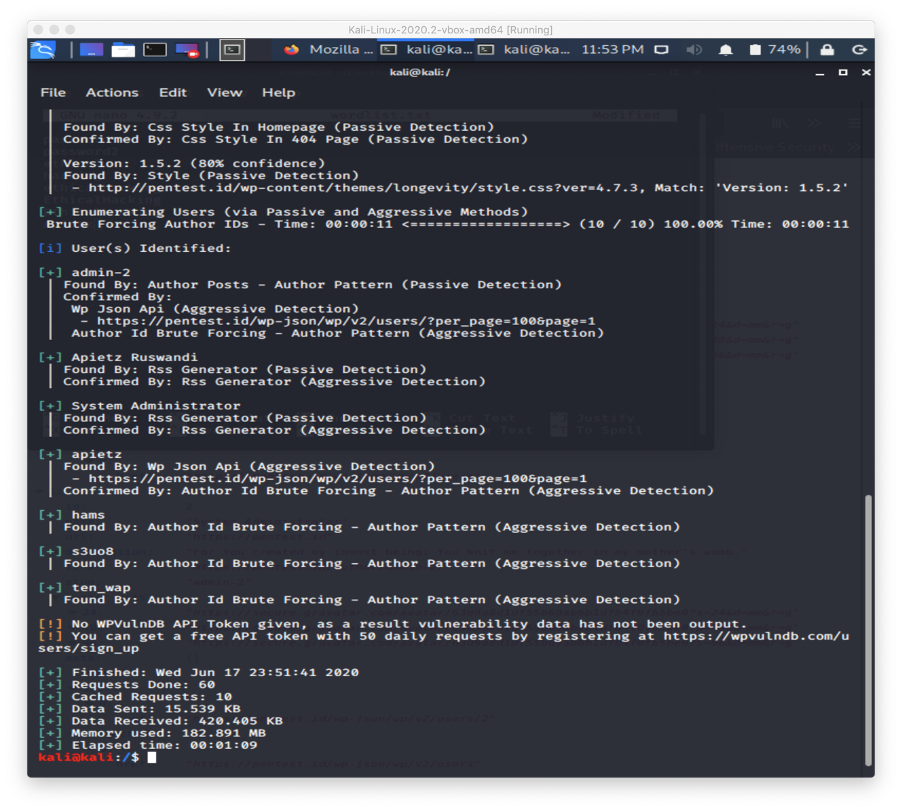
I tried to find the passwords using a brute force attack after I got the valid usernames using the same tool with the help of cupp to generate the list of possible passwords.
I also tried to brute force the FTP server using Metasploit.
We found the vulnerabilities of the website:
Due to missing HTTP headers (Content Security Policy, X-XSS-Protection, HSTS, X-Content-Type-Options, and X-Frame-Options):
- Cross-site scripting (XSS)
- Clickjacking
- MIME Sniffing downgrade attacks
- SSL-stripping man-in-the-middle attacks
- Cookie-hijacking protections weakening.
Unfortunately, I did not manage to break into the website as I cannot find the passwords of the username and XMLRPC Denial of Service had failed to provide us with more valuable information and give us access to the website.
In conclusion, the risk is medium as it is hard to break into the website. However, attackers may design their attacks based on the software server was outdated and that’s why it needs to be updated. The features and components of the website are easily found which need to be avoided such as disabling features like wp-cron.php that may cause vulnerabilities and remove entries from the exposed file like robots.txt. The owner also needs to implement the missing HTTP headers to avoid vulnerabilities.
References:
5 Important Questions to Ask Your Next Penetration Tester. (2015). Retrieved 18 June 2020, from https://blog.redcanari.com/2015/10/26/top-5-questions-to-ask-your-next-penetration-tester/
Pentest-Tools.com. (2020). Website Vulnerability Scanner Report (Light). Pentest-Tools.com.